What data are stored inside Storage Account
Azure Function App uses two subservices blob and files in the Storage Account.
It always creates a two blob containers, called azure-webjobs-hosts and azure-webjobs-secrets.
In the azure-webjobs-hosts container – there are metadata files used for logging purposes, locks etc.
In the container azure-webjobs-secrets you can find really interesting data:
- every function has JSON file
- there is
host.jsonfile, containing all function’s keys, including master FunctionApp key, in encrypted form
Function Apps, not using deployment type app package, also stores even functions source code in File shares container, in the site/wwwroot directory.
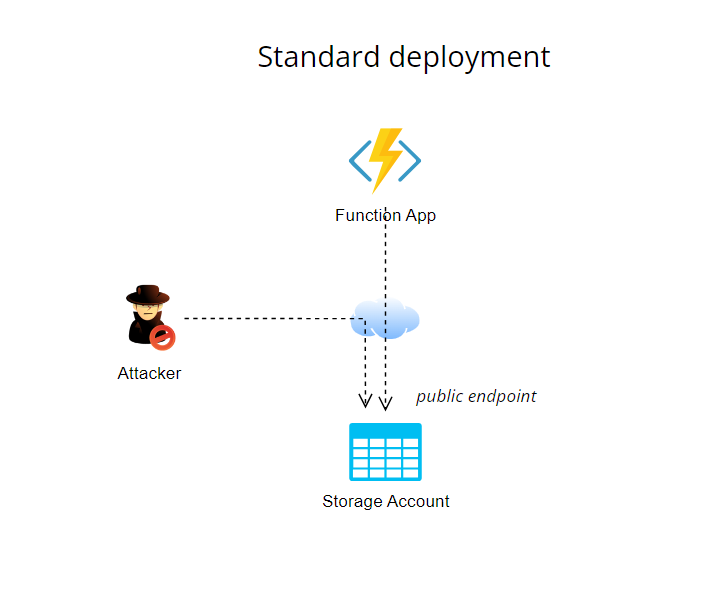
Out-of-the-box setup
When you create a new Function App via standard Azure Portal wizard, it creates automatically a Storage Account. This Storage Account has opened public endpoint and the Function App interacts with storage via SAS (Shared Access Signature) via public endpoint.
This is not so dangerous setup. as you could read it for first time – all file containers in this Storage Account has for Public access level value Private, so you still need to have storage access key for accessing these files.
On the other hand, in this setup, with a combination of some vulnerability, you could get the content on storage easily compromised and for some workloads you need to reduce the risk with adding extra layer of protection.
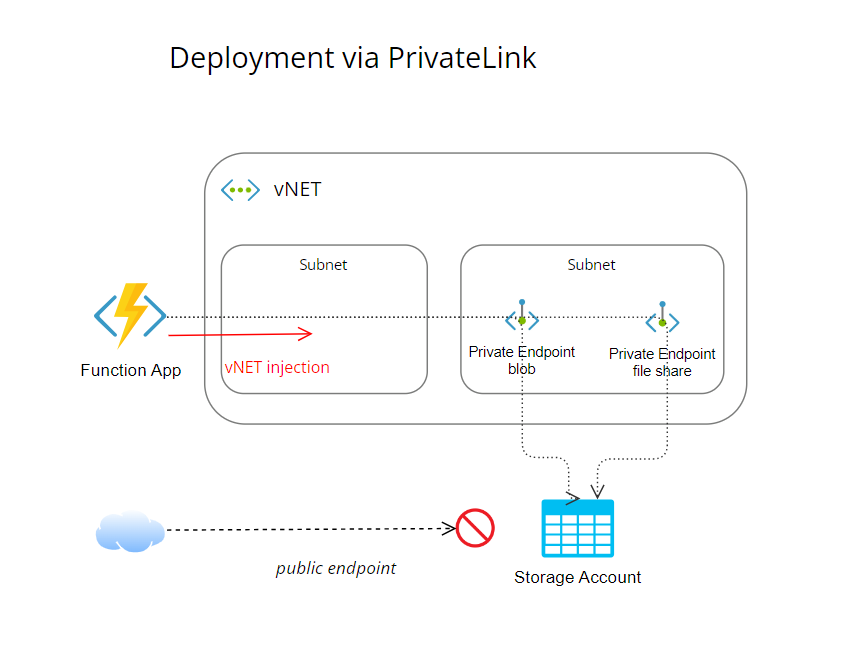
PrivateLink approach
This setup is based on limiting access to the Storage Account and requires having a vNET. Public endpoint of Storage Account is disabled and there is created a PrivateLink endpoint of the Storage Account into Function App’s vNET.
Prerequisites
The Function App need to have a plan supporting vNET integration for egress traffic (higher App Service tier, or for consumption-based resources you need to have a Premium plan).
Storage Account needs to be provisioned as General purpose V2 account kind (V1 is not supported by PrivateLink).
Note
I am reminding this, because it happened to me, that Azure Portal user wizard created a V1 Storage Account for Function App. When this happens, just create a new V2 Storage Account and point the Function App to the new storage resource.
Steps to protect Azure Function (via Azure Portal)
Turn off public endpoint on Storage Account
- Go to
Networking, selectAllow access from selected networksand clickSave
Set up a PrivateLink endpoint for Storage Account
Go to
Networking, select tabPrivate Endpoint connectionsand click on+Private EndpointFollow wizard, as resource select the Storage Account resource
As target sub-resource select
blobvalueRepeat steps, only as a target sub-resource select
filevalue
Set up required feature flag for Function App runtime
- Go to the Function App resource, select
Configurationand select tabApplication settings - Add a new Application settings called
WEBSITE_CONTENTOVERVNET, with value1 - Save new settings
- Test the Function App
Now the Storage Account is not accessible from public internet, but reachable from the Function App.