Introduction
Deploying an Azure Marketplace offer is a powerful way to implement a cloud solution provided by Microsoft’s partners into your Azure subscription, while outsourcing the development to the publisher of the given offer. An offer can be anything from simple solution built on top of Virtual Machines or really complex solutions, utilizing AKS containers and other Azure native services - all these services will be deployed with a purchased offer.
There are two models of a solution in Azure Marketplace:
- Solution template - this plan type enables to deploy a non-transactable solution (Microsoft doesn’t facilitate the payment), where the customer will manage the solution after deployment themselves
- Managed Application - solutions built as Managed Applications enables to deploy a transactable solution, where either the offer’s publisher or the customer manages the solution after deployment
For publisher is there a benefit, that their solution will be displayed in Azure Marketplace, what can help them to accquire new customers.
Managed Application - Introduction
When you deploy a solution based on the Managed Application type, it appears as another resource within your Azure resource group.
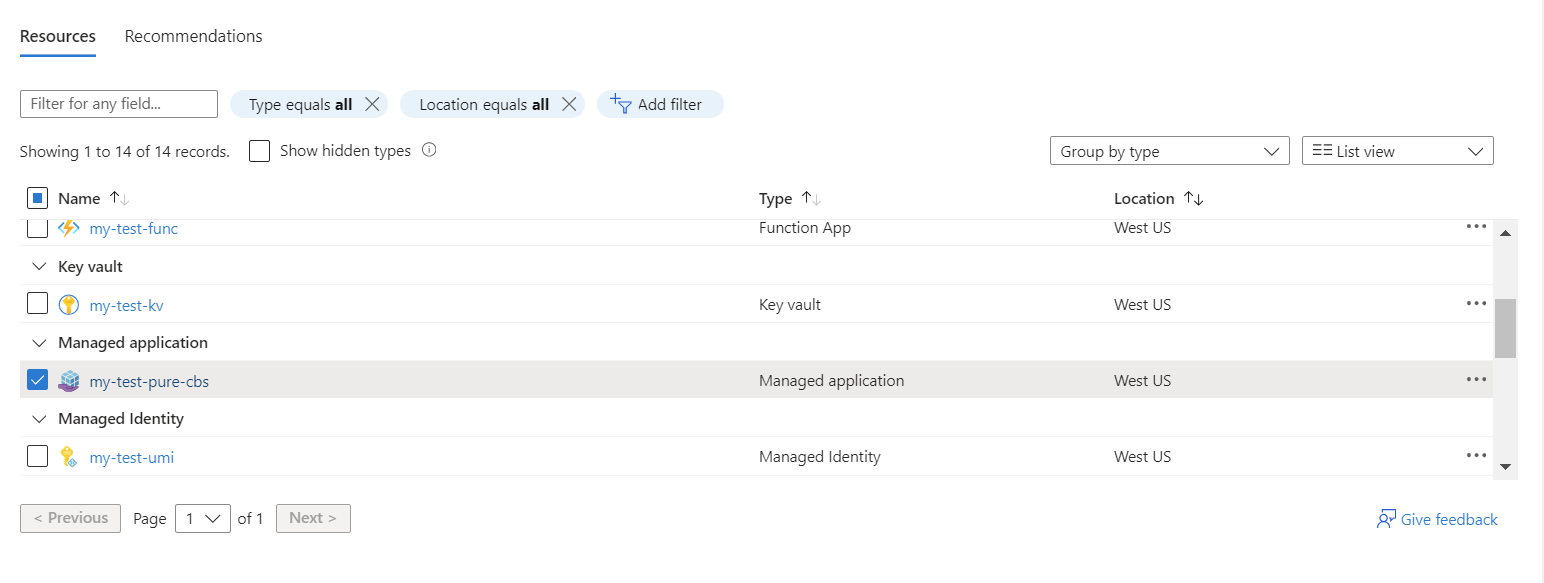

With this resource, a new managed resource group is automatically created within your subscription, where all the necessary resources of solution are deployed.
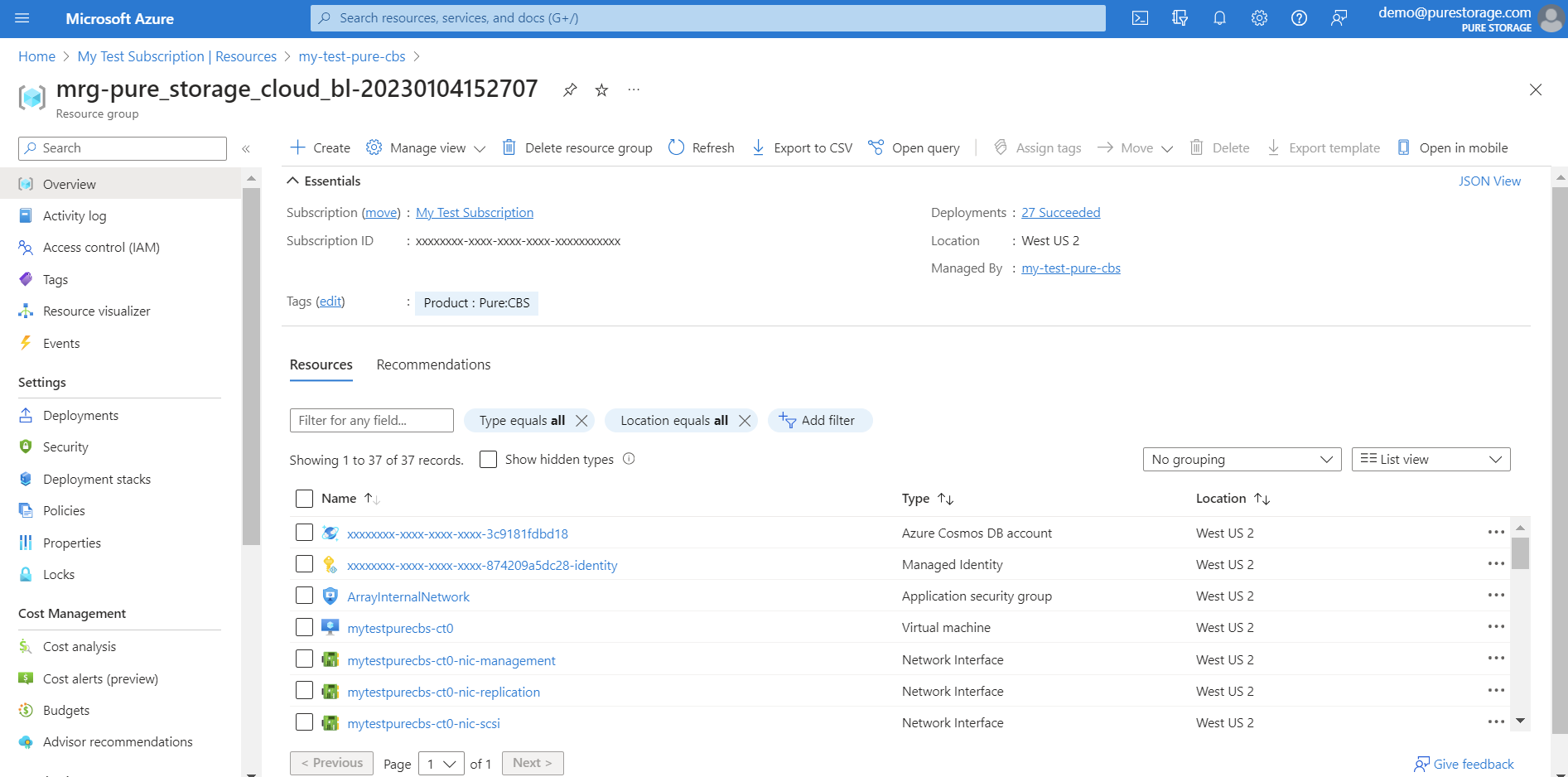
And when you delete the Managed Application resource, Azure Resource Manager will automatically delete the related managed resource group along with all the resources contained within it.
Permissions
A valuable benefit of the Managed Application deployment model is that it allows the publisher to securely access the solution’s resources (within your subscription) using the standard Azure RBAC model. This enables the publisher to monitor, upgrade, or perform maintenance on the solution as needed. The publisher will automatically be granted a Contributor or Owner role for the managed resource group (although this can be opted-out if desired).
It’s a double-edged tool; while it allows customers to out source solution management to the publisher and simply consume it as a service, some customers opt to limit access to reduce their infrastructure’s attack surface. And opting out of management access completely revokes all privileges for the publisher, including read access for monitoring.
Just-in-time Access (JIT)
In response to this challenge, Microsoft has introduced a new feature known as Just-in-time (JIT) access. This feature provides read-only access to the customer’s resources. When necessary, the publisher can request elevated permissions for these resources for a specific time period. The request requires approval from a responsible person on the customer’s side before access is granted.
While this feature effectively addresses the challenge, it has one drawback: it necessitates the use of a Microsoft Entra ID (former Azure Active Directory) P2 license on the customer’s side.
Read-only Access
For customers who lack a P2 License but still need to grant publishers elevated access while maintaining read-only access, there is one available option.
This concept hinges on utilizing the JIT feature, even in scenarios where the customer does not have a P2 License. License detection for JIT occurs during the creation of a JIT access request. If the required license is not present, the request will fail, but the deployment configuration remains unchanged.
As a result, you have the ability to restrict the publisher’s access to solutions that are built on Managed Applications, such as Pure Cloud Block Store.
In this concept, the customer deploys a Managed Application with JIT access enabled and set JIT Approval mode to Manual.
The Approvers list cannot be empty, so you need to add at least one responsible security group or user.
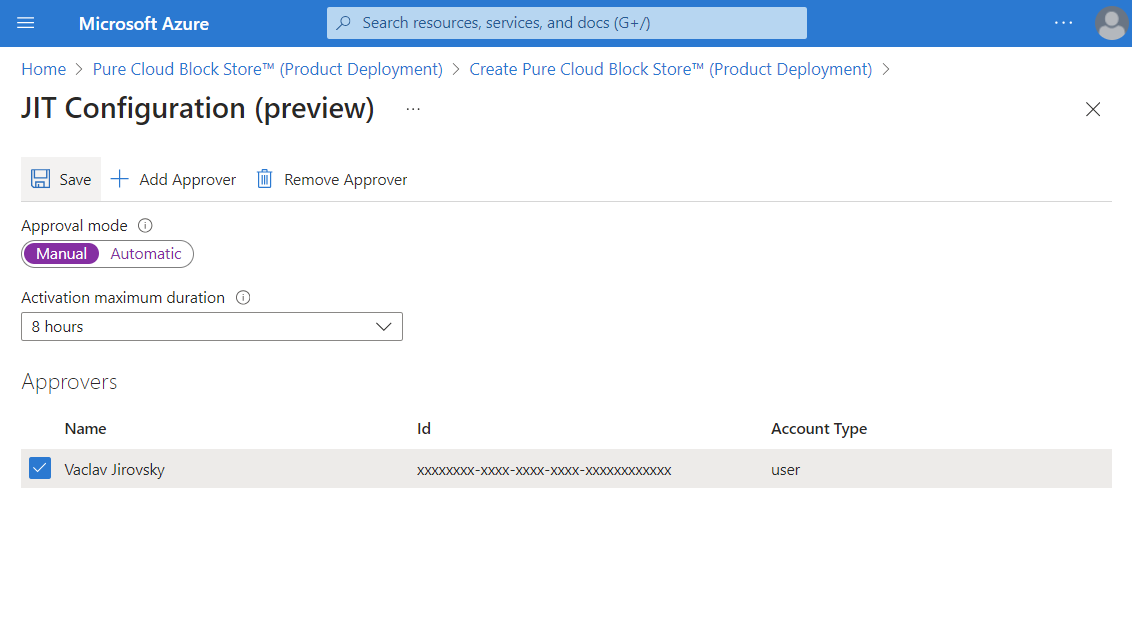
Thanks to the absence of an Microsoft Entra ID license, any attempt by the publisher to gain elevated access will fail, but the publisher still retains desired read-only access, and as a customer, you have more control over your infrastructure.
For customers who have the P2 License, achieving read-only access for publishers is straightforward. Simply set the JIT Approval mode to Manual and refrain from approving any requests.
